
Maintaining many users with various roles and their related security groups can be challenging. For example, you have a user that is in a sales role, but also does basic accounts and a bit of purchasing.
Rather than creating a custom security profile for this staff member, you can add multiple security groups to their card file to define their security access. The merging of these multiple security groups creates their effective security group.
In other words, security groups might be Accounts, Banking, Warehousing, Administration, Purchasing, Banking, etc.
For example:
Security Group |
Security Functions Enabled |
Report Level |
Status Level |
Price Break Movement |
Sales |
Add/edit/view jobs and quotes |
1 |
1 |
1 |
Invoicing |
Mark as Ready and invoicing |
2 |
1 |
1 |
Debtors |
Add payments, etc. |
5 |
5 |
-1 |
Banking |
Allow banking |
10 |
10 |
-1 |
Purchasing |
Add/edit/view purchase orders |
5 |
5 |
-1 |
Security Group |
Security Functions Enabled |
Report Level |
Status Level |
Price Break Movement |
John |
Sales, invoicing |
2 |
1 |
1 |
Mary |
Sales, invoicing, debtors, banking, purchasing |
10 |
10 |
-1 |
In the above example, John’s security is all functions enabled in both the Sales and Invoicing security groups, and the highest level of Report Level, Status Level, and Price Break Movement from the selected security groups.
The Security screen allows better viewing of a user’s effective security, and to view and compare the security of multiple users at the same time. Security settings can also be printed and/or exported.
Adding a User Card File to Multiple Security Groups
To add a user to multiple security groups, edit a user’s card file via CardFiles > View/Edit CardFile (or from a card file list), click Edit, then select the User tab. Click on the ellipsis [...] of the Security selection field, and select the security groups as required.
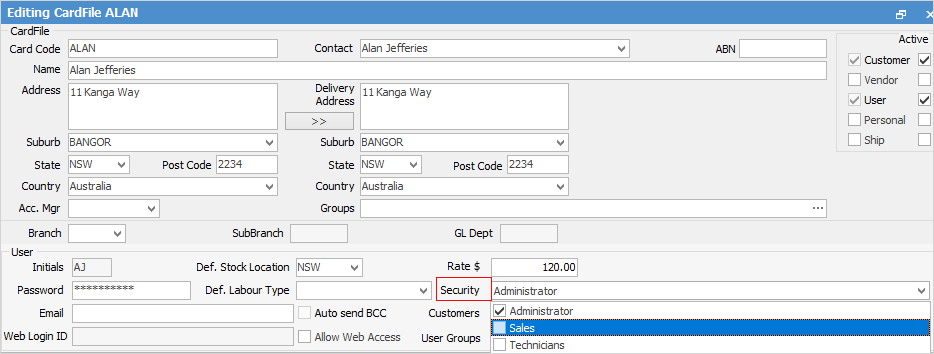
Viewing and Editing Security Groups
When selecting Security, it will appear in the Nav Tree under Tools, allowing the viewing and editing of a user’s card file without having to close the Security screen.
Additionally, the Security form has two further tabs (By User and By Group) to view a user(s) effective security group, and to compare the user(s) security settings.
To view/add/edit security groups, on the ribbon go to Tools > Security.
Viewing a User’s Effective Security Group – By User
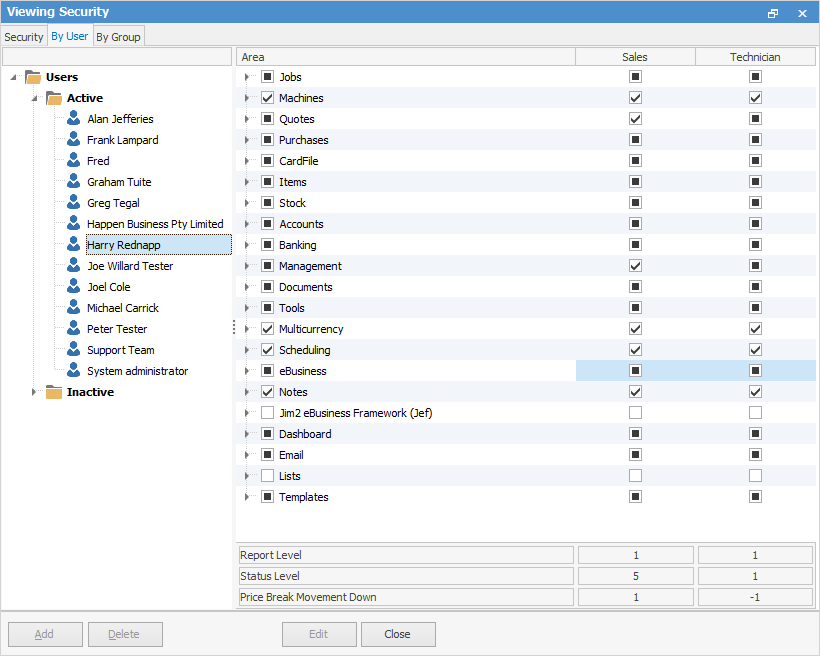
Open Security via Tools > Security and select the By User tab. You will be presented with a tree displaying a list of active and inactive users, and a tree displaying their effective security group and the security groups they belong to.
Select a user, and the security groups that the user belongs to will be displayed, along with their effective security group. This allows an easy way to view exactly why a user has access to certain areas and functions in Jim2 based on the security groups they belong to.
You can right click on a user to view or edit their card file and which security groups they belong to.
You can also right click in the right-hand tree to print or export a user’s security settings.
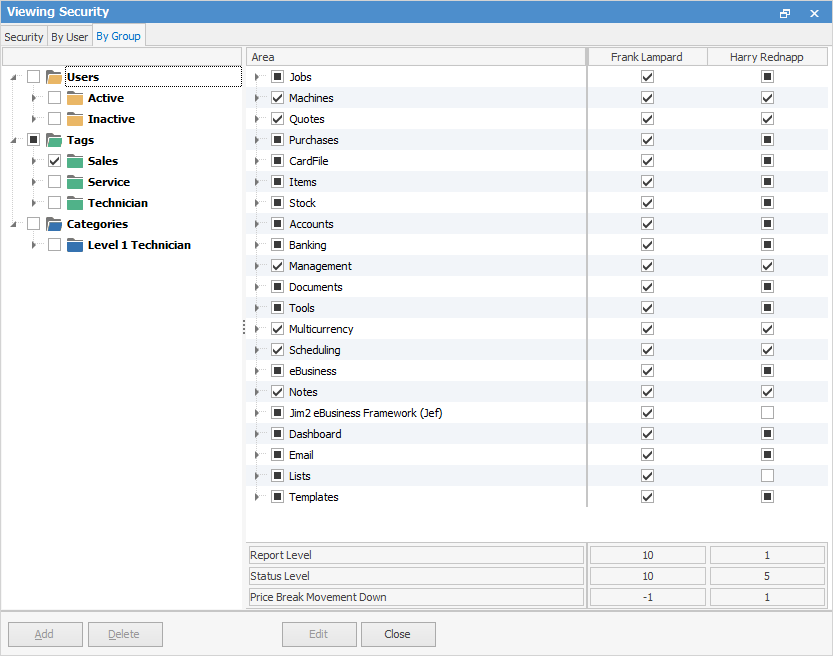
Viewing and Comparing Security of Multiple Users – By Group
Open Security via Tools > Security and select the By Group tab. You will be presented with a tree displaying a list of active and inactive users, along with user group categories and tags.
Ticking one or more tick boxes will display those users, along with their effective security groups. For example, clicking on the Active folder will display all active users. Clicking on a User Group (Tags > Sales for instance) displays all users in that user group.
You can right click on a user to view or edit their card file and the security groups they belong to.
You can also right click in the right–hand tree to print or export the selected user’s effective security group settings.
Further information: