
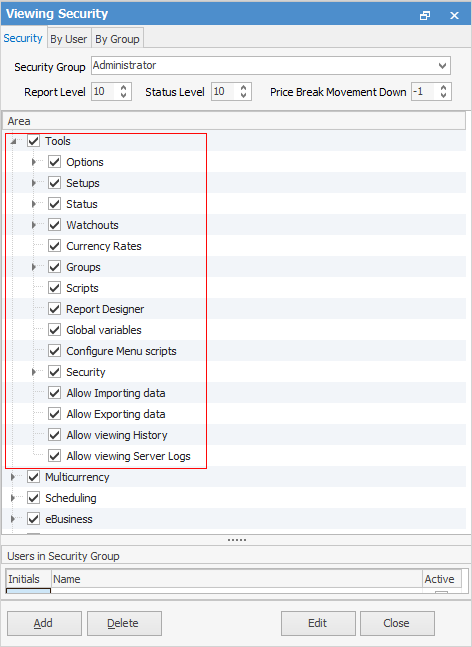
Image showing security settings for Tools within Jim2
 |
All security settings are active (enabled) for all security groups, until edited.Only users with the appropriate administrative rights can add/edit security. |
When setting up security, consider organisational structure, workflow and employee usage requirements. Jim2 is designed as a multi-user application and, although allowing all users to have high level or unrestricted access to all functions may be appropriate in a small business, larger sites will probably want to limit employee work functions by using the security options available.
 |
If users are well trained on the interactive and flow-on effects of changes that they can make to existing defaults within Jim2, the level of security that management will need to implement will be reduced.
If users receive a security warning, the administrator should be made aware of the sequence of events that caused it, and provide additional training to the user, or change that user's security settings to something more appropriate.
Security should be used to complement the Options, Setups and automated warnings that Jim2 already has in place. Setting security measures to restrict access to Jim2 functions should be performed to prevent untrained users from performing functions, or pre-empting accidental data changes in areas that are particularly sensitive to the company workflow.
There are some functions which have a roll-on effect when chosen as secured areas. For example, if a security group is nominated to not be able to view jobs, that group won't be able to view a list of jobs.
Within Jim2, security level is identified by security groups, tags and categories. Each employee can belong to more than one security group, tag or category, and has access rights to certain areas and functions within Jim2 that have been set up for those particular security groups, tags and categories. User security overrides certain settings in Tools > Options.
When reports are devised, they are identified by ascending report levels – the higher the number, the more sensitive company information the report contains. Security groups must include an appropriate report level.
There are a large number of functions within Jim2 that can be restricted from use via Security. The option of allowing or denying any user or group the right to access any or all of those functions is available. |
|
When setting up Jim2 for the first time, there is a default user called sys, with a password of sys. The sys cardfile belongs to the security group of Administrator, thereby always providing sys access rights to set and edit security groups. Jim2 prevents the sys security group and card code from being changed, except for the password (see below), ensuring that there is always the option to set and edit security groups, in case access to security is accidentally set as denied to all other users.
Once cardfiles have been set up for other users with a security group of Administrator, it would be wise to change the default password of the cardfile sys (via the User tab in the cardfile for sys), as this default password is commonly known. This will prevent users from logging on as sys and changing security options. |
Please see the individual Jim2 objects (ie. Job, Quote, etc.) for more detailed information on each object's security.
Jobs Security in the Help File index
Further information
How to
