The ability to add, edit, view and amend the Schedule, etc. is handled via Jim2 Security.
To enable other users to view specific areas, select the Security Group, click Edit and expand the Scheduling (and sub-folder) checkbox.
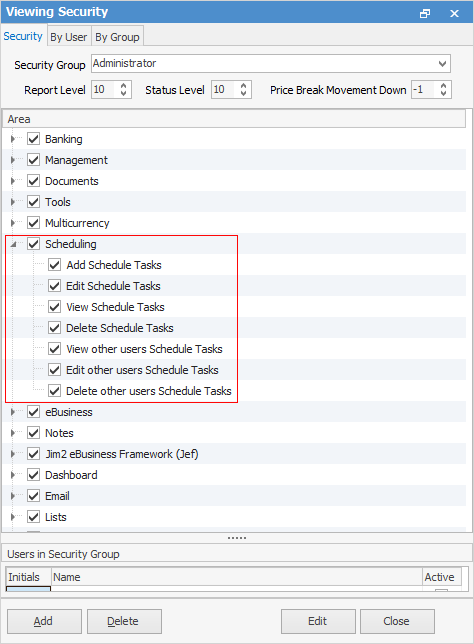
The image above shows all the security settings available for scheduling, all self explanatory.
Choose what the user is able to do.
Checkbox settings:
Checkboxes |
Explanation |
|---|---|
|
Will only return results for what is ticked. |
|
Will not return results for any unticked boxes. |
|
Will return results for all of the above. |
Please see User Group – Tags/Category Groups for more in-depth information on Scheduling security.
Further information


